
Children of the Cold War
An apocalyptic legacy is being used to build data centers ready for the next major disaster

An apocalyptic legacy is being used to build data centers ready for the next major disaster
Want a reliable data center? You need to understand how contamination happens - and how to prevent it

Terrorists and Russia are highlighted as risks to international connectivity

With extreme weather comes associated risks. Don’t let complacency ruin your data center
Prevention is better than cure but sometimes the worst happens. We meet the specialist forensic engineers who can root out the causes of a data center failure

In the last seven years, LinkedIn has taken charge of its data center destiny. Head of IT Sonu Nayyar tells us how

Accreditation doesn’t make the data center, but it can certainly play a part helping the sales team shift the racks

Do you trust everyone with a key to your kingdom?

Modern data centers need to keep up with best practice, a DCD event is told

To get businesses onto its cloud, Google will have to win users’ trust. Here are the tools it developed for the job

Can federal employees convince the White House to make data centers a priority?

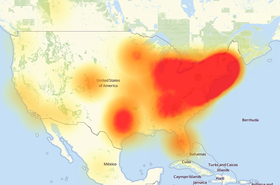
Northern California and Maine fail to receive crucial data

People are the weakest link. The latest version of Windows helps prevent foolish admin errors and phishing

A new president. A lot at stake

The fourth in our series: what happens when President Trump runs US surveillance?

No matter what you do, someone will be able to get in. But you should still do these things.

The zettastructure is evolving to handle the Internet of Things. It will change every part of our technology infrastructure

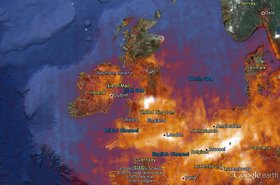
IoT devices, botnets and state warfare shape the future of Internet traffic

London semi-finals bring budding cyber security trainees to BAE and HMGCC

When a stockpile of cyber weapons surface, Russia and US tensions flare, while vendors pick up the pieces

Blockchain underpins the Bitcoin currency, but you can do a whole lot more with it

A recent report explored data center risk. A second one looked at power usage. We analyze both

Current security tools can’t wade through all the data: OpenSOC calls on big data techniques and open source

Traffic within your data center is more at risk than that coming through the perimeter. Micro-segmentation can ease your worries