In early March 2021, a hacker group publicly exposed the username and password of an administrative account of a security camera vendor. The credentials enabled them to access 150,000 commercial security systems and, potentially, set up subsequent attacks on other critical equipment. A few weeks earlier, leaked credentials for the collaboration software TeamViewer gave hackers a way into a system controlling a city water plant in Florida (US). They remotely adjusted the sodium hydroxide levels to a dangerous level (the attack was detected, and harm avoided).
These are just some of the most recent examples of exploits where critical infrastructure was disrupted by remote access to IT systems, including some high-profile attacks at power plants.
The threat of cybersecurity breaches also applies to physical data centers, and it is growing. Cloud computing, and increased automation and remote monitoring have broadened the attack surface. (See our recent report Data center security: Reassessing physical, human and digital risks.)
How widespread is this?
So, how widespread is the problem of insecure facility assets? Our research of vulnerable systems on the open Internet suggests it is not uncommon.
For close to a decade, the website Shodan has been used by hackers, benevolent and malevolent, to search for targets. Instead of fetching results that are webpages, Shodan crawls the internet for devices and industrial control systems (ICSs) that are connected to the internet but exposed.
Shodan and similar search engine websites (BinaryEdge, Censys and others) provide a compendium of port-scan data (locating open ports, which are a path to attack) on the Internet. Expert users identify interesting characteristics about certain systems and set out to gain as much access as they can. Automation tools make the process more efficient, speeding up and also expanding what is possible for an exploit (e.g., by defeating login safeguards).
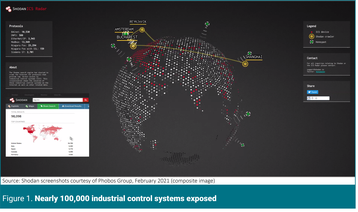
In a recent demonstration of Shodan for the Uptime Institute, the cybersecurity firm Phobos Group showed more than 98,000 ICSs exposed globally, including data center equipment and devices. Phobos quickly discovered access to the login screens of control systems for most major data center equipment providers. In Figure 1 (as in all figures), screenshots of aggregate search results are shown with specific details hidden to ensure privacy.
The login process itself can be highly problematic. Sometimes installers or users do not change the default credentials supplied by the manufacturers, which can often be found online. During our demonstration, for example, Phobos used a default login to gain access to the control system for cooling units supplied by a widely used data center equipment vendor. If this exercise were carried out by a genuine intruder, they would be able to change setpoint temperatures and alarms.
Users’ customized login credentials can sometimes be obtained from a data breach of one service and then used by a hacker to try to log into another service, a type of cyberattack known as credential stuffing. The availability of lists of credentials has proliferated, and automated credential-stuffing tools have become more sophisticated, using bots to thwart traditional login protections. (Data breaches can happen without leaving any trace in corporate systems and can go undetected.)
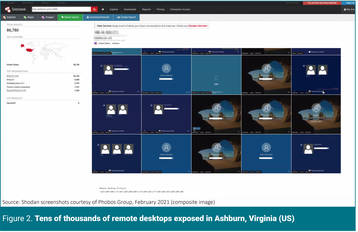
As cybersecurity exploits of critical infrastructure in recent years have shown, control system interfaces may be the primary targets — but access to them is often through another system. Using the Shodan tool, the security company Phobos searched for exposed remote desktops, which can then provide access to multiple systems. This method can be particularly troubling if a control system is accessible through a remote desktop and if the user employs the same or similar passwords across systems.
There are many remote desktops exposed online. As Figure 2 shows, in a recent Shodan search, over 86,700 remote desktops were exposed in the US city of Ashburn, Virginia, alone (a city known as the world’s data center capital). This list includes a set of addresses for a global data center capacity provider (not shown).
Password reuse is one of the biggest security vulnerabilities humans introduce, but it can be minimized with training and tools, and by multifactor authentication where practicable. Installers and users should also be prevented from removing password protection controls (another vulnerability that Phobos demonstrated). There are also cybersecurity tools to continuously scan for assets exposed online and to provide attack simulations. Services used at some facilities include threat intelligence and penetration tests on IP addresses and infrastructure. Low-tech approaches such as locked workstations and clean-desk policies also help protect sensitive information.
Cybersecurity of data center control systems and other internet protocol (IP)-enabled assets is multilayered and requires a combination of ongoing strategies. The threat is real and the likelihood of physical breaches, unauthorized access to information, and the destruction of or tampering with data and services is higher than ever before.