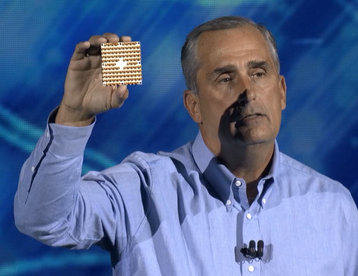
At the 2018 Consumer Electronics Show in Las Vegas, Intel detailed its latest efforts to build quantum and neuromorphic computing chips.
The company unvelied Tangle Lake, a 49-qubit superconducting quantum test chip, and Loihi, a neuromorphic research chip. Both represent early steps, with Intel admitting that a lot of research still has to be done in both fields before they could become commercial products.
One small step
“In the quest to deliver a commercially viable quantum computing system, it’s anyone’s game,” Mike Mayberry, corporate VP and MD of Intel Labs, said.
“We expect it will be five to seven years before the industry gets to tackling engineering-scale problems, and it will likely require one million or more qubits to achieve commercial relevance.”
Intel hopes to eventually build a complete quantum computing system, from architecture to algorithms to control electronics, with Tangle Lake representing initial progress towards this goal.
The latest batch of silicon comes two months after delivery of a 17-qubit test chip.
“This 49-qubit chip pushes beyond our ability to simulate and is a step towards quantum supremacy, a point at which quantum computers far and away surpass the world’s best supercomputers,” Intel CEO Brian Krzanich said during his CES keynote.
“We expect to solve key technical challenges that must be overcome to move quantum computing forward. It’s quite a bit more work required than just this chip but this is a major breakthrough in quantum computing.”
The company also talked about its neuromorphic research chip, codenamed Loihi, which is meant to mimic basic operation of the brain.
“This has been a major research effort by Intel and today we have a fully functioning neuromorphic research chip,” Krzanich said. “This incredible technology adds to the breadth of AI solutions that Intel is developing.”
Intel plans to share the Loihi test chip with universities and research institutions in the first half of the year.
The elephant in the room
Of course, there was a shadow hanging over Intel’s keynote - the major security flaw present in over a decade’s worth of its processors, that, to some extent, also impacted AMD, Arm and IBM.
Krzanich addressed the matter at the beginning of his speech:
“Today is a day when we all come together to celebrate the lifeblood of our amazing industry – and that’s really about innovation. But before we start, I want to take a moment to thank the industry for coming together for another purpose – to address the recent security research findings reported as Meltdown and Spectre.
“The collaboration among so many companies to address this industry-wide issue across several different processor architectures has been truly remarkable. Security is job number one for Intel and our industry. So, the primary focus of our decisions and our discussions have been to keep our customer’s data safe.
“As of now, we have not received any information that these exploits have been used to obtain customer data. And we are working tirelessly on these issues to ensure it stays that way. The best thing you can do to make sure your data remains safe is to apply any updates from your operating system vendor and system manufacturer as soon as they become available.
“For our processors, products introduced in the past five years, Intel expects to issue updates for more than 90 percent of them within a week and the remaining by the end of January. We believe the performance impact of these updates is highly workload-dependent. As a result, we expect some workloads may have a larger impact than others, so we will continue working with the industry to minimize the impact on those workloads over time.”
AMD had previously criticized the efforts to paint both Meltdown and Spectre as industry-wide issues. It said in a statement: “To be clear, the security research team identified three variants targeting speculative execution. The threat and the response to the three variants differ by microprocessor company, and AMD is not susceptible to all three variants. Due to differences in AMD’s architecture, we believe there is a near zero risk to AMD processors at this time.”
The vulnerabilities were originally set to be officially revealed after the CES keynote, but were announced prematurely after media coverage.