Zero Trust is one of the defining concepts of modern information security. Zero Trust recognizes that security is always in flux and simply because a user was safe an hour ago doesn’t mean that remains true now. As a result, every access to data must be re-evaluated based on all available security contexts.
However, many organizations don’t apply these concepts when it comes to their data. Just like end-user laptops, enterprise data is constantly on the move – being downloaded, shared, copied, modified, and transformed across user devices and applications both internally and in the cloud. Organizations also have many types of sensitive data, and most don’t stay tucked away in well-defined enclaves. And as data moves and spreads, so does an organization’s risk.
To keep pace, Zero Trust policies must be able to follow sensitive data regardless of where it goes or how it is used. Policies need to understand the full context of a given piece of data and its risk to the organization, regardless of how many hands (or apps) it passes through. Zero Trust must be applied not only when data is accessed, but also every time it is shared or used.
New data-centric approaches to security are making this possible and empowering organizations to extend their Zero Trust strategy in very powerful and practical ways. Let’s look at a few examples.
Adding data context to Zero Trust decisions
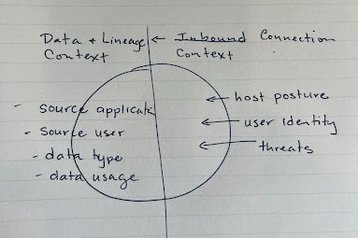
Zero Trust policies often focus on the traits of the inbound connection. For example, tools may scan incoming traffic for exploits or malicious content. Likewise, policies will verify the user’s identity and may check the security posture of the connecting device.
These are great perspectives but they only tell half of the story. In addition to evaluating who or what is connecting to the data, we also need to know exactly what they are connecting to. For example, Data Detection and Response (DDR) tools can identify and protect sensitive data based on the application or user that originally created it.
Now instead of just knowing the context of the incoming user and laptop, organizations can also know that the user is trying to access HR data that came from the corporate Workday app or a company roadmap created by the CEO. Likewise, data-centric controls can learn how employees and groups use and collaborate on certain types of data, then ensure that data doesn’t spill beyond those users who have an actual need for it.
Getting out of the enclave mindset
Zero Trust forces organizations to think beyond traditional perimeter-based security. Many assets live outside the perimeter, and threats may already be inside the perimeter. No connection is implicitly trusted and every access to sensitive data should be analyzed.
This directly applies to data as well. In the same way that enterprises are no longer defined by a monolithic perimeter, most sensitive data is no longer defined by tightly-controlled enclaves. Users download data, collaborate, share, and transform it into countless derivatives. Instead of being confined in silos, most data exists as a self-replicating cloud that constantly spreads throughout the enterprise.
Why is this important? Well, if organizations want to apply Zero Trust to their sensitive data, they have to recognize that their data is a moving target. Zero Trust can’t just be applied to a specific application or subnet. Policies and protections must follow the data that needs to be protected.
Data sharing is as important as data access
The “enclave” mindset can also lead to security policies that are almost entirely based on controlling access to data. However, it is just as important to understand and control what happens to data after that access is granted. Unfortunately, many security teams lose visibility and control over their data once it has been downloaded or copied by an end-user.
However, this is arguably when Zero Trust is the most important. When data is in an application or a database, there is typically one well-controlled road to the data. But once that data is on a user’s device, there are countless ways that it can be shared or modified. Files can be renamed, copy/pasted, converted to new file formats, uploaded to the cloud, encrypted, shared over chat, or countless other applications.
Adding data-centric controls not only tells organizations where their sensitive data is but also lets them control how it is shared. This should be relatively intuitive from a Zero Trust perspective – just because a user is allowed to access data should not imply that they are then blindly trusted to properly handle the data going forward.
One of the most challenging aspects of Zero Trust is that it forces us to seek out our own blind spots. It is natural for organizations to overlook data-centric controls simply because they haven’t been possible in the past. However, new advancements in data security allow organizations to understand the full history and context of any piece of data in their environment. This context can and should play a critical role in Zero Trust architectures going forward. To keep data safe, security teams must be prepared to follow it wherever it goes.