Attacks against supervisory control and data acquisition (SCADA) systems have doubled over the last year, according to research data compiled by Dell SonicWall. Finland was the primary target of these attacks, followed by facilities in the UK and US – not surprisingly, Dell observed, since internet-connected SCADA systems are more common in these countries.
The most common threat trends in the “2015 Dell Security Annual Threat Report” come from observations by the Dell SonicWALL Threat Research Team, with research data gathered through the company’s Global Response Intelligence Defense (GRID) Network. Dell’s GRID Network compiles information from more than one million security sensors in more than 200 countries, in addition to data from honeypots in its threat centers, reputation data from global firewall and email security devices, and information it receives from global industry groups, research organizations, and freelance security researchers.
In terms of raw data, the number of attacks has increased each of the last few years: Dell saw worldwide SCADA attacks increase from 91,676 in January 2012 to 163,228 in January 2013, up to 675,186 in January 2014.
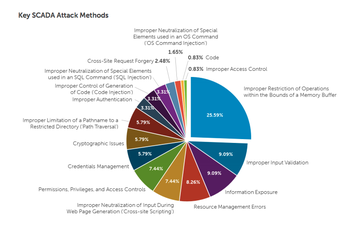
Buffer overflow vulnerabilities accounted for a quarter of the attacks observed by Dell in the research. More than a dozen other methods were used to execute the remaining attacks.
“Since companies are only required to report data breaches that involve personal or payment information, SCADA attacks often go unreported,” said Patrick Sweeney, executive director for Dell Security. “This lack of information sharing combined with an aging industrial machinery infrastructure presents huge security challenges that will to continue to grow in the coming months and years.”
Equipment age indeed is a significant challenge with respect to SCADA hacks. While not all attacks can be prevented for internet-facing systems, Dell has suggested seral mitigation techniques to limit exposure. To protect against SCADA attacks, in general, it suggests you: ensure all software and systems are up to date; ensure your network only allows connections with approved IPs; follow operational best practices for limiting exposure, such as restricting USB ports if they aren’t necessary and ensuring Bluetooth is disabled; and report and share information about SCADA attacks with the wider industrial community so that it is aware of emerging threats.
Targeting Data Centers
SCADA systems are large-scale, computer based industrial control systems that monitor and control processes at most of the world’s critical infrastructure facilities. Industrial and critical infrastructure facilities were thought to be the primary targets of SCADA attacks, but data centers could increasingly fall into this category.
In a recent interview with DatacenterDynamics, Ed Ansett, a leading expert on critical facilities, said there are many devices and systems within today’s data centers that could be targeted by cyber attackers. It includes cooling systems, generators, switchgear, motor control centers, universal power supplies (UPS) or batteries connected to servers, air conditioning systems, plumbing systems used to circulate chilled liquid around a data center, fire suppression systems, and security systems.
“They comprise programmable logic controllers (PLC), distributed control systems (DCS), SCADA systems, and other software-based plant control systems,” Ansett explained.