Some users of Amazon Web Services have noticed their cloud server instances slowing down after applying security patches that tackle Intel’s Meltdown security vulnerability.
The security fixes move the operating system kernel into its own separate virtual memory space, which can slow down the system. It remains unclear how widespread such performance degradation is.
Slow your horses
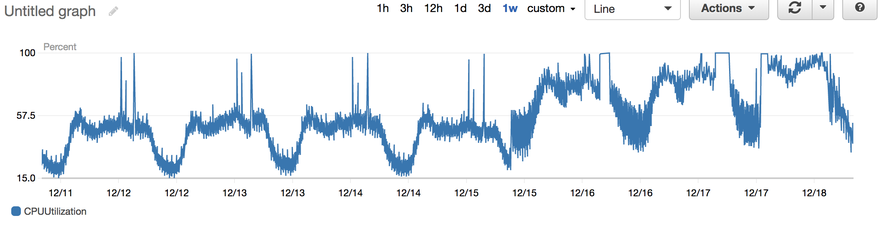
“Immediately following the reboot my server running on this instance started to suffer from CPU stress,” one admin said in an AWS discussion thread first spotted by The Register, where users shared tales of the impact.
“Looking at CPU stats there was a very clear change in daily CPU usage pattern, despite continuing normal traffic to my server. I performed extensive review of what might have changed on my server configuration but drew a complete blank - configuration of the server did not change.”
The admin also shared an image of the sudden change in CPU usage:
Another admin, sfdanb, concurred: “We are experiencing the same thing across all roles in our fleet.”
Yet another said: “Our paravirtual c3 was crippled by the update, but our HVM lost 30 performance of its performance overnight too. I also appreciate that this is not Amazon’s fault. But some prior warning that instances would lose performance on certain dates was necessary so we could take pre-emptive action. Instead we had to put up with the crisis we had this morning due to Amazon’s silence.”
An AWS support employee confirmed that “the update that is being applied to a portion of EC2 instances can, in some corner cases, require additional CPU resources.”
While we are reporting on AWS complaints here, it is important to note that this is an industry-wide issue, with Google Cloud Platform, Microsoft Azure and others rolling out updates that may impact performance - depending on the type of workload.