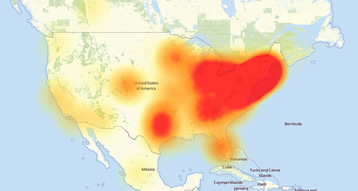
A global distributed denial of service (DDoS) attack on Dyn’s DNS infrastructure made numerous online services inaccessible for a large number of users, particularly those living on the east coast of the US.
The exact scale of the attack and the reasons for it are yet unknown, but comes at a time of increasing DDoS activity.
A growing threat
“Starting at 11:10 UTC on October 21st-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure,” Dyn said in a status post.
“Some customers may experience increased DNS query latency and delayed zone propagation during this time. Updates will be posted as information becomes available.”
Later, the company added that “this attack is mainly impacting US East and is impacting Managed DNS customers in this region. Our Engineers are continuing to work on mitigating this issue.”
According to Dyn, services were restored at 13:20 UTC.
Customers suffering from disruption included Twitter, SoundCloud, Spotify, Netflix, Reddit, Pagerduty, Shopify, Disqus, Freshbooks, Vox Media, PayPal, Etsy, Github, Heroku, Time, PlayStation, the Intercom app and more. While Dyn said that the issue has been resolved, users of the affected services were still reporting problems with connectivity at time of writing.
Amazon Web Services was also impacted by the Dyn’s temporary collapse, and said: “Between 4:31 AM and 6:10 AM PDT, we experienced errors resolving the DNS hostnames used to access some AWS services in the US-EAST-1 Region.
“During the issue, customers may have experienced failures indicating “hostname unknown” or “unknown host exception” when attempting to resolve the hostnames for AWS services and EC2 instances. This issue has been resolved and the service is operating normally.”
Update: At 10:03 AM PDT (17:03 UTC) AWS said: “On October 21, 2016 between 4:30 AM and 6:11 AM PDT, some AWS customers experienced errors establishing connectivity to a small number of AWS endpoints hosted in the Northern Virginia (“US-EAST-1”) Region. We observed similar impact between 9:26 AM and 9:46 AM PDT in the Ireland (“EU-WEST-1”) Region.
“These events were caused by errors resolving the DNS hostnames for some AWS endpoints. AWS uses multiple DNS service providers, including Amazon Route53 and third-party service providers. The root cause was an availability event that occurred with one of our third party DNS service providers. We have now applied mitigations to all regions that prevent impact from third party DNS availability events.
“During these events, core AWS functionality and all security controls continued to operate normally. Customers that independently utilize the third party DNS service provider may continue experiencing errors resolving DNS names hosted with that provider.”
Update 2: As of 20:37 UTC, the DDoS attack on Dyn is still occurring, intermittently.
Dyn’s status page says: “Our engineers are continuing to investigate and mitigate several attacks aimed against the Dyn Managed DNS infrastructure.”
Update 3: More details here.
We previously reported on a major DDoS attack on cyber security researcher Brian Krebs, measuring at 620 Gbps - at the time, the largest DDoS ever recorded. Since then, that record was broken by an attack on French hosting firm OVH that was roughly double that of Krebs.
Many of these more recent attacks make use of IoT devices such as routers and cameras to flood the target’s systems.
Last month, a hacker known as ’Anna_Senpai’ released the source code for Mirai, a tool that uses IoT devices for DDoS attacks. The malware continuously scans the Internet for IoT systems protected by factory default or hard-coded usernames and passwords, before taking control of such systems.
Indeed, security intelligence firm Flashpoint believes that it has observed a Mirai botnet attacking Dyn, and that it was responsible for today’s outages.
But DDoS attacks only last as long as the traffic can be sustained. Elsewhere, we have seen far greater long-term damage caused by hacks of big businesses, NSA zero days leaking into the wild, and the growing rate of state-sponsored cyberwarfare attacking political structures.