GitHub, the code hosting and collaboration platform that supports some of the world’s most active software projects, was briefly taken offline this week by a distributed denial of service (DDoS) attack.
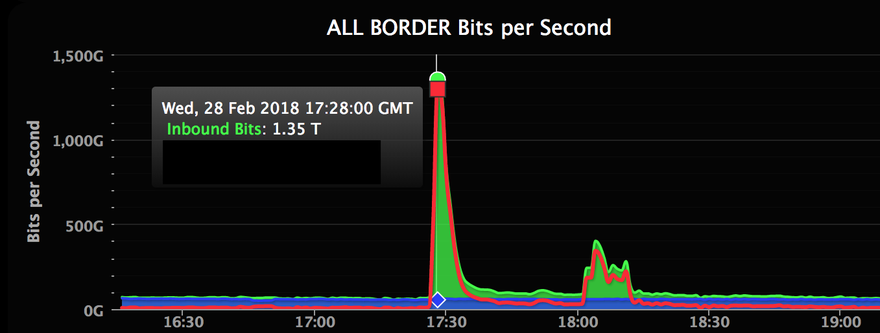
The website was unavailable for approximately 30 minutes on Wednesday after being hit with up to 1.35Tbps in bogus traffic – making this the largest DDoS attack on record.
To prevent similar attacks in the future, the company will continue investing in infrastructure automation, deploying additional transit capacity and partnering with content delivery networks (CDNs) and Internet exchanges.
“We understand how much you rely on GitHub and we know the availability of our service is of critical importance to our users. To note, at no point was the confidentiality or integrity of your data at risk,” GitHub’s site reliability engineer Sam Kottler said in a blog post.
Who would do such a thing?
As of April 2017, GitHub had almost 20 million users and maintained 57 million repositories, making it the largest host of source code in the world.
The attack against the platform used the memcached protocol and UPD port 11211. According to Cloudflare, this “obscure” amplification attack vector is used to send forged requests to a vulnerable UDP server.
The UDP server consumes resources to prepare the response – which is fine if such requests arrive one by one, but can easily overwhelm the network when thousands of requests are sent all once.
The attack is effective because the response packets are much larger than the request packets - Cloudflare says an proficient attacker with just 1Gbps of IP spoofing capability can easily ‘amplify’ the attack to reach 100Gbps of bandwidth.
According to Kottler, the particular technique used against GitHub enabled an amplification factor of up to 51,000. It originated from more than a thousand different autonomous systems, across tens of thousands of unique endpoints and peaked at 1.35Tbps, reaching 126.9 million packets per second.
“Making GitHub’s edge infrastructure more resilient to current and future conditions of the internet and less dependent upon human involvement requires better automated intervention,” he said.
“We’re investigating the use of our monitoring infrastructure to automate enabling DDoS mitigation providers and will continue to measure our response times to incidents like this with a goal of reducing mean time to recovery (MTTR).”
“We’re going to continue to expand our edge network and strive to identify and mitigate new attack vectors before they affect your workflow on GitHub.com.”