Growth projections for cloud computing should make data center operators smile, especially when “the cloud” is floating in the middle of their data center. One reason for the upbeat forecast is decision-makers are warming up to the idea that cloud computing and virtualization may be secure, or at least as secure as what they currently have. But is it?
Several years ago, Trend Micro voiced concern. “These new platforms (cloud computing and virtualization) open additional avenues for threats against data, systems, and reputation,” warned the report Security Threats to Evolving Data Centers. “For the most part, these threats are presented through the same types of attacks — data-stealing malware, web threats, spam, phishing, Trojans, worms, viruses, spyware, bots, and more.”
Most feel those concerns are now pretty much under control. But the report referenced several subtle concerns that continue to plague data center operations, in particular, smaller venues. They include communication blind spots, instant-on gaps, inter-VM attacks and hypervisor compromises, mixed-trust level VMs, and resource contention. Let’s look at each in turn.
Communication blind spots
Most legacy network security devices are unable to scan traffic between VMs located on the same host server. The report suggests using a dedicated scanning security VM on the host server to control and examine inter-VM communications.
However, the report warns that this approach (scanning security VMs) is not ideal for a cloud environment, adding, “In the cloud, protection is best provided as self-defending VMs. Protection is self-contained on each VM and does not require communication outside of the VM to remain secure.”
Instant-on gaps
One of the most appreciated features of virtualization is the ability to provision, migrate, put into service, and then decommission VMs rapidly to support variable in-house and customer demands. What concerns the Trend Micro authors are VMs that have been inactive.
“After a period of time, dormant VMs can eventually deviate so far from the baseline security state that simply powering them on introduces significant security vulnerabilities,” explains the report. “And even if VMs are dormant, attackers may still be able to access them.”
Another problem is cloning VMs from templates that have out-of-date security. “Even when VMs are built from a template with virus protection and other security applications, the VMs need the security agent to have the latest security configurations and pattern file updates.”
The solution is once again a dedicated security VM on each host server. When the VM is activated or cloned, the security VM automatically updates the VM before it is put into use.
Inter-VM attacks and hypervisor compromises
Something seemingly forgotten is that virtualized servers use the same operating systems and applications as physical servers. Thus, they are vulnerable to all of the same threats. The Trend Micro authors offer several examples they have encountered.
- An attacker can compromise one guest VM, which is used to infect other guest VMs on the same host server. The authors suggest, “Firewall and intrusion detection/prevention systems need to be able to detect malicious activity at the VM level, regardless of the location of the VM within the virtualized environment.”
- Hyperjacking is an attack where a user takes control of the host server’s hypervisor by first compromising a guest VM and using it to attack the hypervisor. If successful, the hypervisor will then be used to attack the remaining uninfected guest VMs.
- The report notes that application programming interfaces (APIs) are prime targets for malicious code, adding, “There is a risk that, owing to the rapid change in the API space and the current race to market, virtualization management systems will not be secure in the future.”
Mixed-trust level VMs
The Trend Micro authors voice concern over servers that host both mission-critical VMs and non-critical VMs, resulting in what they call mixed-trust level VMs. The authors then mention one way to fix that is to segregate VMs into groups of similar security requirements. However, that defeats the purpose of having a virtualized environment.
“Enterprises need to ensure that mission-critical information is protected while still realizing the benefits of virtualization,” write the authors. “With self-defending VM security, VMs can remain safe even in mixed trust level environments, with protection such as intrusion detection and prevention, a firewall, integrity monitoring, log inspection, and antivirus capabilities.”
Resource contention
Resource utilization is a problem when antivirus and security applications meant for physical servers are applied to VMs. The worst case scenario results in what the authors call an Antivirus Storm. “This storm is like a run on the bank, where the bank is the underlying virtualized resource pool of memory, storage, and CPU. This performance impact hampers server applications and VDI environments.”
Virtualization-aware technology, the report emphasizes, will minimize resource usage, especially when increasing VM densities on a host server.“A dedicated scanning VM can coordinate staggered scans across VMs to preserve host resources,” the report says. “And agent-less antivirus removes the antivirus software from the guest VMs and centralizes these functions on the dedicated security VM, enabling a massive reduction in memory footprint for security on virtual hosts.”
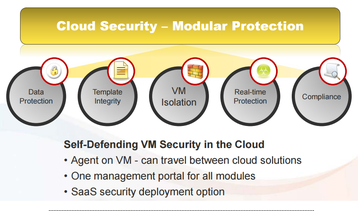
The report’s authors placed a great deal of emphasis on something called “self-defending VM security.”
This concept is explained in a more recent report, Virtualization and Cloud Computing: Best Security Practices which describes the concept as:
“VM-level protection by creating a security perimeter around each VM. This way, the enterprise can co-locate applications with different trust levels on the same host and can defend VMs in a shared, multi-tenant environment…. And VM-level protection allows VMs to stay secure even as VMs travel between different environments – from on-premise virtual servers to private clouds to public clouds, and even between cloud vendors.”
Virtualization-aware technology, the report emphasizes, will minimize resource usage, especially when increasing VM densities on a host server.“A dedicated scanning VM can coordinate staggered scans across VMs to preserve host resources,” mentions the report. “And agent-less antivirus removes the antivirus software from the guest VMs and centralizes these functions on the dedicated security VM, enabling a massive reduction in memory footprint for security on virtual hosts.”
Self-defending VM security
The report’s authors placed a great deal of emphasis on something called “self-defending VM security.” However, they did not explain what they meant by this. That information can be found in the Trend Micro reporVirtualization and Cloud Computing: Best Security Practices which describes the concept as:
“VM-level protection by creating a security perimeter around each VM. This way, the enterprise can co-locate applications with different trust levels on the same host and can defend VMs in a shared, multi-tenant environment…. And VM-level protection allows VMs to stay secure even as VMs travel between different environments – from on-premise virtual servers to private clouds to public clouds, and even between cloud vendors.”
Ultimately, security must travel with the data
Four years ago or today, data center security operations, to meet customer needs must focus on the data, ensuring its security wherever it travels: on-premise in the virtualized environment, in the cloud, and now even on mobile devices.