While Windows Server has been ubiquitous in the business environment for most of the 21st century, the migration of the corporate world to virtualization and the cloud has left Microsoft playing catch-up. Without question VMware has led the way when it came to providing a virtualized infrastructure, and, in combination with virtual machines running Linux has become the most commonly deployed server infrastructure.
Bigger, better more secure VMs
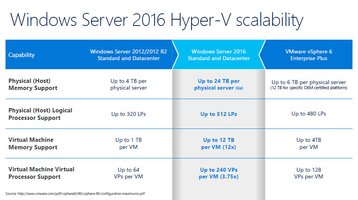
Microsoft has learnt from its popular Azure cloud infrastructure, and given Windows Server 2016 a hypervisor that supports significantly more scalable VMs than Windows Server 2012. According to published information about VMware, that’s also more than the most recently announced version of vSphere6 Enterprise Plus. As you can see from the Microsoft-provided chart, the increase in capability for an individual VM is significant. This upgrade in capability will likely make the VM environment suitable for almost any workload.
In keeping with the theme of Windows Server 2016 being more secure and efficient, the most important new feature set may well be virtualization security, in the form of the guarded fabric and shielded VMs.
First, consider the logic behind this; in its simplest form, a VM and the data therein is simply a file on storage media somewhere. All of the perimeter and network security in the world can’t protect the information in that VM from someone who has physical access and can simply copy that VM file to media that can be dropped in a pocket and walked out the door. Once that VM file has left the building it can be mounted and dissected by an attacker with ill intent.
Shielding VMs
With a shielded VM, that virtual machine gets much of the security you would expect on a physical server such as disk encryption, TPMs, and secure boot. The generation 2 shielded VM, when fully configured, simply can’t be used outside of the host network because it requires the Host Guardian Service feature in Windows Server 2016 to decrypt the VM so that it can be run. The HGS has the keys to the kingdom; it literally controls the encryption keys to its VMs. The information is found nowhere else so a VM can’t be removed from the protected environment and accessed.
The Host Guardian Service has two primary components; the Attestation service, which evaluates if the host system is valid, and the Key Protection Service, which determines if the key should be released to any given request. The HGS should be configured to run on a cluster within the enterprise, with fail-over, so that it is always available to provide the needed access to shielded VMS.
With HGS and shielded VMs, even physical access won’t allow the most common types of attacks. In addition to the encrypted VM, even moving the VM to an unsecured host within the enterprise won’t work; only trusted hosts, with their unique identifier known to the HGS can launch the VM. And in that situation it runs with all of its security in place.
Attaching a debugger to a trusted host won’t work; the HGS checks for the presence of a debugger before releasing the key. Attempting to install malware on a host is also checked for, nor can malware be added to a shielded VM image, as only templates that match known healthy configurations can be booted. The Attestation Service constantly measures the metrics of known good VMs and hosts prior to boot. It checks against known good configurations and is specifically aware of things such as debuggers which can be used to compromise systems. If a VM doesn’t make it past that Attestation Service it never even gets a chance to have a key issued to allow it to boot.
Two security levels
This is significantly more security than can be provided by simply using a virtual TPM and encryption. In that configuration the fundamental issue is that anything someone with administrator credentials can do can be undone by someone with an equivalent level of access. If you run a Virtual TPM inside the VM, the encryption keys remain in memory and are therefore available to be hacked.
Generation 2 VMs, in addition to being used like the previous generation of VM, support two different security levels; Shielded and Encryption Supported. Shielded VMs are seriously locked down. The common day to day administration methodologies currently in use, such as PowerShell Direct or direct VM console connections are not available with a shielded VM. The administrator accustomed to using RDP to look at a hosted server will need to adjust the management behavior.
That being said, however, an enterprise can deploy encrypted VMs that will still get the benefit of the secure encrypted VM, while being configurable and allowing the use of more common administrative tools as well as a virtual machine console.
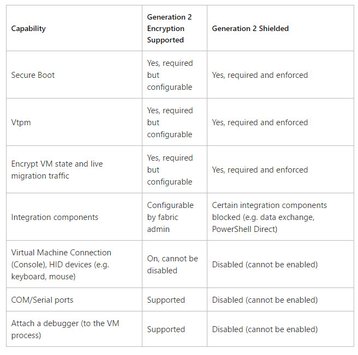
The table above, provided by Microsoft, shows the differences between Gen2 encrypted and shielded VMs. Keep in mind that tis technology, as it applies to VMs, is operating system agnostic. Windows Server, various Linux varieties, and any other supported operating system can be hosted in a VM and get all of the benefits derived from either form of generation 2 virtual machine. A demo of shielded VMs can be found here.
Answering customer concerns
When you talk to data center operators about what their customer concerns are, they almost always lead with security regardless of whether the operator is running colocation or cloud services or anywhere in between. “How can you guarantee the security of my applications and data?” is an issue that all of these operators are facing on a daily basis. With Windows Server 2016 Microsoft is providing a variety of answers which can be tailored to the specific needs of the data center operator. None of the solutions are required of contradictory allowing operators to provide any client with whatever level of security for which they wish to contract.
So, it’s early to say whether this version of Windows Server can achieve data center dominance, but the security features are a definite step in the right direction