Research by cyber security vendor Bitdefender suggests that huge numbers of corporate servers are being hijacked to mine cryptocurrencies, with their owners left footing massive electricity bills.
The practice called ‘cryptojacking’ is looking to compromise large pools of physical computers, cloud infrastructure and even legitimate websites to collectively mine on cyber criminals’ behalf.
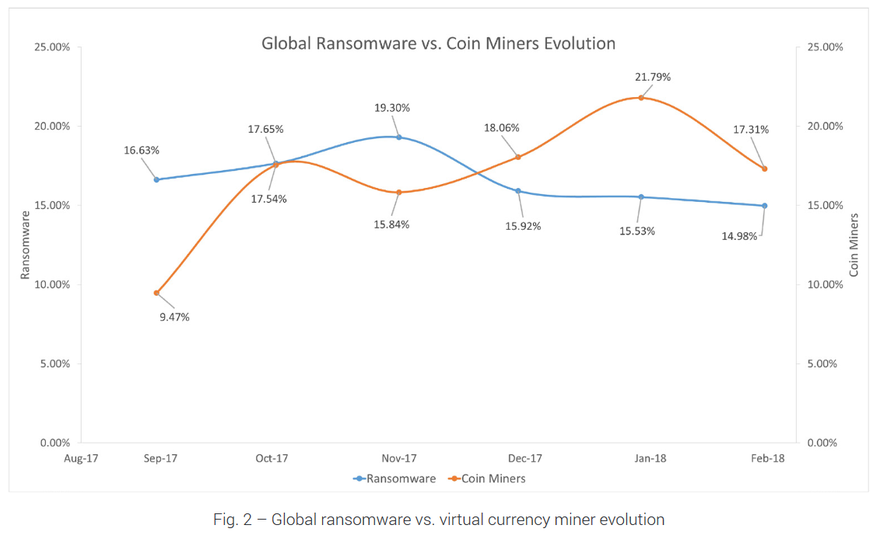
According to Bitdefender, the number of reports on ‘crypto miners’ increased by 130 percent between September 2017 and January 2018, making this type of attack more popular than last year’s bogeyman, ransomware. Prior research by Forrester noted that corporate servers, followed by employee-owned devices and corporate-owned devices, are the most-targeted devices for cryptocurrency mining.
How it’s made
Cryptocurrencies like Bitcoin and Ethereum are based on an open source, peer-to-peer protocol. The concept was first introduced in 2009 by an anonymous developer known only as ‘Satoshi Nakamoto’.
Due to their decentralized and anonymous nature, Bitcoin and its derivatives were originally used online among parties interested in keeping their transactions secret, hence their reputation as tools for tax evasion and cyber crime.
In recent years, however, the technology has gone mainstream: we have seen an explosion of new cryptocurrencies, and online businesses have started accepting some as a form of payment.
Minting new cryptocurrency ‘coins’ is an energy-intensive process that involves complex mathematical operations. Today, most industrial-scale mining operations rely on specialized equipment that utilizes ASICS – application-specific integrated circuits. The same process can also be carried out on standard server CPUs, although with much lower efficiency.
According to Bitdefender, corporate data centers with large pools of resources present the perfect target for cyberjacking, and since cyber criminals don’t pay for electricity, this approach is much more profitable than mining legally, using own hardware.
“Data centers usually allow organizations to scale their business by letting them optimize costs and computing resources based on their immediate requirements. However, if virtual infrastructures become compromised and cloud admins lose authentication credentials via searching attacks, social engineering, or unpatched security vulnerabilities, cybercriminals seize control,” explains the whitepaper.
“From there, it’s just a matter of spinning up powerful and resource-intensive rogue virtual instances that come pre-installed with cryptocurrency mining malware.
“Since it may take several weeks – or until the bill comes in – to spot rogue virtual hosts, hackers would have already mined tens or hundreds of thousands worth of cryptocurrency while the affected organization is left holding the power/services bill.”
Bitdefender telemetry has shown that cryptocurrency-enabled malware has displaced another popular type of malware – ransomware. Ransomware-related reports were outnumbering crypto-miner reports until the beginning of December 2018, when the situation reversed.
The company noted that the preferred method for compromising corporate servers remains leveraging unpatched systems or exploiting unknown vulnerabilities, so this trend is expected to continue.